Information security is not a new topic now. Information security in the communication system is naturally the most critical. However, due to the particularity of the GPON network, which is a P2MP (point to multi-point) network, a PON port of an OLT can communicate with a bunch of (usually 64) ONU, so does it have a unique information security mechanism? If so, what is this information security mechanism? And how is it established?
Communication is a two-way street. First, let’s look at the downstream of GPON, that is, OLT sends data to ONU.
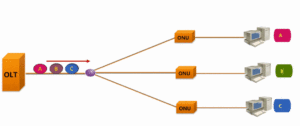
GPON downstream transmission
As we know, the downstream transmission of GPON is broadcast, that is, the PON port on the OLT side encapsulates the data sent to the ONU by the GEM frame and sends it to all ONUs in broadcast. All ONUs can receive the same data. Only the GEM PORT ID is used to filter its own data (the GEM PORT ID of different ONUs under the same PON PORT is different).
If a malicious user programs an ONU to remove the data filtering mechanism that should be there, then he can monitor all users’ data, which is obviously unsafe.
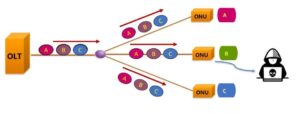
Therefore, the data in the downlink direction must be encrypted, and the encryption algorithm used is AES-128 (Advanced Encryption Standard, 128-bit key). In addition, it is required that the data sent to a certain ONU cannot be decrypted by other ONUs, the encryption key of each ONU needs to be unique and private.
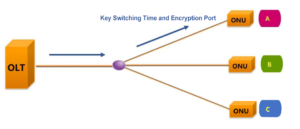
Next, let’s look at the encryption process of the AES-128(taking ONU A as an example).
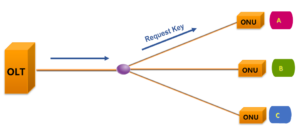
(1)First, the OLT opens the encryption process and requests the key from the downstream ONU A.
(2)Second, ONU A generates the encryption key and sends it back to the OLT.
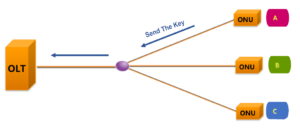
(3)Finally, the OLT defines the key switching time and encryption port, and notifies ONU A.
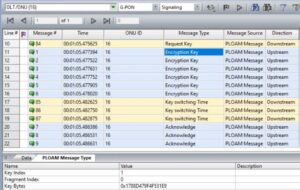
Give another example of encrypted message interaction in GPON. The following figure shows the establishment process of the encryption mechanism between a PON port and its ONU of it(ONU ID:16).
1. Request Key: The OLT requests the key from the ONU.
2. Encryption Key: The ONU responds and sends the generated new key to the OLT in two parts, and repeats it three times.
3. Key Switching Time: After the OLT receives the new key, it starts the key switch and notifies the ONU of the frame number using the new key through the relevant command, also three times.
4. Acknowledge: The ONU responds to the key switching request from the OLT.
Let’s look at how the upstream direction of the GPON system (i.e., the ONU sends data in the direction of the OLT) ensures data security.
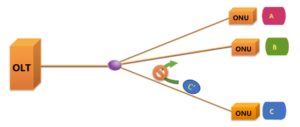
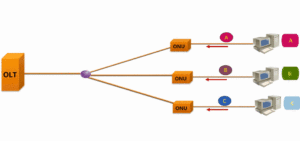
In fact, as shown in the figure, due to the physical characteristics of the GPON network, the optical splitter does not have a data exchange function. When ONU C sends data to the upstream OLT, it will not reach ONU B or ONU A. Therefore, other ONUs cannot obtain the data from ONU C. That is, the upstream data transmission between ONUs is isolated, which naturally avoids the interception of information between each other. In the GPON system, there is no encryption for the upstream data.
We know that in a communication system, it is rarely necessary to measure the distance between the two ends when the transceiver sends data. However, in the PON network, we need the PON port on the OLT side to distance the ONU attached below. Why is this?
Do you remember the networking topology of PON? PON is a point-to-multipoint (P2MP) networking architecture. One PON port on the OLT side can connect to multiple ONUs, and TDMA is used for upstream data transmission.
The distance between the ONU attached to the same PON port and the OLT is different. The shortest distance can be tens of meters, and the longest distance can be up to 20 kilometers. Those who study optical communication know that there is a transmission latency of light over the fiber, which is about 5us/km.
In order to achieve TDMA access, and ensure that the uplink data of each ONU is inserted into the specified time slot after the trunk fiber convergence, there is no collision and large gap between each other, OLT must accurately measure the distance between each ONU and OLT, so as to control the time when each ONU sends upstream data.
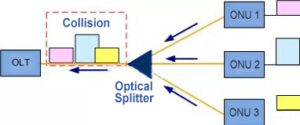
Data conflict will occur without ranging
Therefore, in a word, the purpose of PON system ranging is to avoid time slot conflict (collision) in the upstream direction of ONU.
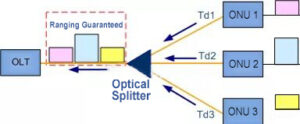
Ranging ensures that upstream data do not conflict
In addition, due to the changes in ambient temperature and device aging after the PON system runs for a period of time, the transmission delay will also change continuously. OLT also needs to continuously distance the ONU to ensure the stable operation of the PON network.
Related Products:
-
 GPON-ONU-CLB+ GPON ONU SFP TX-1.25G/RX-2.5G TX-1310nm/RX-1490nm Class B+ 20km SC/UPC SMF DDM Transceiver Modules (Not GPON ONU STICK,NO MAC function)
$15.00
GPON-ONU-CLB+ GPON ONU SFP TX-1.25G/RX-2.5G TX-1310nm/RX-1490nm Class B+ 20km SC/UPC SMF DDM Transceiver Modules (Not GPON ONU STICK,NO MAC function)
$15.00
-
 GPON-OLT-B+ GPON OLT SFP TX-2.5G/RX-1.25G TX-1490nm/RX-1310nm Class B+ 20km SC SMF DDM Transceiver Modules
$25.00
GPON-OLT-B+ GPON OLT SFP TX-2.5G/RX-1.25G TX-1490nm/RX-1310nm Class B+ 20km SC SMF DDM Transceiver Modules
$25.00
-
 GPON-OLT-40B+ GPON OLT SFP TX-2.5G/RX-1.25G TX-1490nm/RX-1310nm Class B+ 40km SC SMF DDM Transceiver Modules
$30.00
GPON-OLT-40B+ GPON OLT SFP TX-2.5G/RX-1.25G TX-1490nm/RX-1310nm Class B+ 40km SC SMF DDM Transceiver Modules
$30.00
-
 GPON-OLT-C++ GPON OLT SFP TX-2.5G/RX-1.25G TX-1490nm/RX-1310nm Class C++ 20km SC SMF DDM Transceiver Modules
$30.00
GPON-OLT-C++ GPON OLT SFP TX-2.5G/RX-1.25G TX-1490nm/RX-1310nm Class C++ 20km SC SMF DDM Transceiver Modules
$30.00
-
 GPON-OLT-C+ GPON OLT SFP TX-2.5G/RX-1.25G TX-1490nm/RX-1310nm Class C+ 20km SC SMF DDM Transceiver Modules
$30.00
GPON-OLT-C+ GPON OLT SFP TX-2.5G/RX-1.25G TX-1490nm/RX-1310nm Class C+ 20km SC SMF DDM Transceiver Modules
$30.00
-
 GPON-OLT-60C+ GPON OLT SFP TX-2.5G/RX-1.25G TX-1490nm/RX-1310nm Class C+ 60km SC SMF DDM Transceiver Modules
$38.00
GPON-OLT-60C+ GPON OLT SFP TX-2.5G/RX-1.25G TX-1490nm/RX-1310nm Class C+ 60km SC SMF DDM Transceiver Modules
$38.00






