1. The concept of firewall
The firewall, also known as a protective wall, was invented by Check Point founder Gil Shwed in 1993 and introduced to the international Internet (US5606668(A) 1993-12-15). It is a network security system that sits between the internal network and the external network.
It is an information security protection system that allows or restricts the passage of transmitted data according to specific rules.
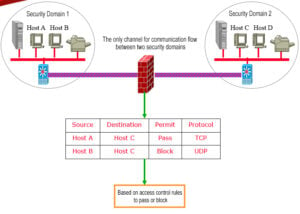
In the network world, it is the communication packets that carry the communication data that are filtered by the firewall. In the network, the “firewall” refers to a method of separating the intranet from the public access network (the Internet), which is actually an isolation technology. A firewall is a scale of access control implemented when two networks communicate, which allows people and data that you “agree” to enter your network while keeping people and data that you “disagree” with out, maximizing the chance of preventing hackers in the network from accessing your network. In other words, if you don’t through the firewall, people inside your company can’t access the Internet, and others on the Internet can’t communicate with people inside your company.
2. The history of firewall
Since its birth, firewall has gone through four development stages.
- Firewall Based on Router
- Customized firewall tool-sets
- Firewall built on general purpose operating system
- Firewall with a secure operating system
The common firewalls now are firewalls with secure operating systems, such as NETEYE, NETSCREEN, TALENTIT, etc.
3. The types of firewall
Network Level Firewall
A network-level firewall can be considered as an IP packet filter that operates on the underlying TCP/IP protocol stack. It can be enumerated to allow only packets that match certain rules to pass through, while the rest are prohibited from passing the firewall (except for viruses, which cannot be prevented). These rules can usually be defined or modified by the administrator, although some firewall devices may only be able to apply the built-in rules.
Application Firewall
The application firewall operates at the “application layer” of the TCP/IP stack, where the data streams you generate when using a browser or when using FTP belong. An application layer firewall intercepts all packets to and from an application and blocks others (usually by simply dropping them). In theory, this type of firewall can completely block the data flow from outside to the protected machine.
Database Firewall
A database firewall is a database security system based on database protocol analysis and control technology. Based on an active defense mechanism, it realizes database access and behavior control, dangerous operation blocking, and suspicious behavior auditing. Through SQL protocol analysis, the database firewall allows legal SQL operations to pass and blocks illegal and non-compliant operations according to predefined prohibition and permission policies, forming the peripheral defense circle of the database and realizing active prevention and real-time audit of dangerous SQL operations. Database firewall provides SQL injection prohibition and database virtual patch package function in the face of the invasion from outside.
4. Linux Firewall
Linux firewalls are very useful in enterprise applications, examples are as follows.
- Small and medium-sized enterprises and Internet cafes have iptables as a NAT router, which can be used to replace traditional routers for saving costs.
- IDC server rooms generally do not have hardware firewalls, and servers in IDC server rooms can use Linux firewalls instead of hardware firewalls.
- iptables combined with squid can be used as a transparent proxy for internal Internet access. Traditional proxies need to configure the proxy server information in the browser, while iptables + squid transparent proxy can redirect the client’s request to the proxy server port. The client does not have to make any settings and does not feel the presence of the proxy.
- When using iptables as an enterprise NAT router, you can use the iptables extension to block P2P traffic and also block illegal web pages.
- iptables can be used to map external IP to internal IP.
- Iptables can easily prevent lightweight DOS attacks such as ping attacks and SYN flood.
- In summary, Iptables has two application modes: host firewall and NAT router.
5. The basic principle of firewall
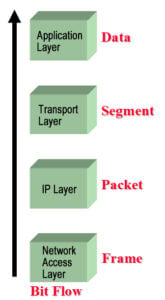
Corresponding to the flow of byte transmission in the figure below, it can be divided into the following layers:
- Packet filtering: works at the network layer, it determines whether to allow packets to pass or not based only on the IP address, port number, protocol type, and other flags in the packet header.
- Application Proxy: works at the application layer, and by writing different application proxies, it realizes the detection and analysis of application layer data.
- Stateful Inspection: works at layer 2~4, access control are the same as 1, but the object of processing is not a single packet, but the whole connection, through the rule table and connection status table, comprehensive judgment whether to allow the packet to pass.
- Complete Content Inspection: works at layers 2~7, it not only analyzes packet header information and status information but also restores and analyzes the content of application layer protocols to effectively prevent hybrid security threats.
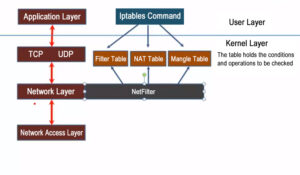
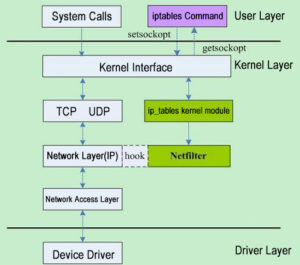
6. Netfilter and iptables
Netfilter is a Linux 2.4 kernel firewall framework proposed by Rusty Russell, which is both simple and flexible and can implement many functions in security strategy applications. Such as packet filtering, packet processing, ip masquerading, transparent proxy, dynamic Network Address Translation (NAT), as well as user and Media Access Control (MAC) address-based filtering and state-based filtering, packet rate limiting, etc. These rules of Iptables/Netfilter can be flexibly combined to form a very large number of functions and cover various aspects, all thanks to its excellent design ideas. The Netfilter/Iptables packet filtering system can be treated as a whole, with netfilter as a kernel module implementation and iptables as a tool for upper-level operations. Without a strict distinction, in Linux both netfilter and iptables can be considered to refer to the Linux firewall. In fact, Iptables is a tool that manages kernel packet filtering and can be used to configure rules in the kernel packet filtering form. It runs in user space.
The difference is that netfilter is a new packet filtering engine introduced in the Linux 2.4 kernel, called Netfilter, which refers to the internal structure of the packet filtering firewall in the Linux kernel, not in the form of programs or files, and belongs to the “kernel state” firewall function system. iptables refers to the command program used to manage the Linux firewall, usually located in /sbin/iptables, which is part of the “user state” firewall management system. iptables is the tool that controls Netfilter, the older sibling of the command ipchains in the Linux 2.2 kernel. The iptables is the tool that controls Netfilter and is the older sibling of the ipchains command in the Linux 2.2 kernel.
The rules set by Netfilter are stored in kernel memory, while iptables is an application-level application that modifies the XXtables (Netfilter’s configuration table) stored in kernel memory through the interface put out by Netfilter. These XXtables consist of tables, chains, and rules. iptables is responsible for modifying this rules file at the application layer. firewalld is similar to it.
What is the connection between iptables and netfilter?
Many people immediately think of iptables as a firewall, but in fact iptables is not a firewall, it is just software or a tool that can write certain rules and save the written rules to netfilter’s rule database. Therefore, the real “fire prevention” is Netfilter, not iptables. netfilter is a framework in the kernel, which contains four tables and five chains, and these chains contain a lot of rules. The rules that the packets are compared to are the rules defined in this chain.
In the following, we will refer to the Linux firewall as iptables.
7. The performance of firewall
Throughput: This metric directly affects the performance of the network.
Latency: the time interval between the arrival of the last bit of the input frame at the ingress and the output of the first bit of the output frame at the egress.
Packet loss rate: the percentage of frames that should be transmitted by network devices under steady-state load, but are dropped due to lack of resources.
Back-to-back: Starting from the idle state, a significant number of fixed-length frames are sent at a transmission rate that reaches the minimum legal interval limit of the transmission medium. The number of frames sent when there is a loss of the first frame.
Simultaneous Browser Connections: The maximum number of simultaneous connections that can be established between hosts passing the firewall or between a host and the firewall.
8. The limitation of firewall
Although the firewall is a basic facility to protect network security, it also has some security threats that are not easy to prevent: first of all, the firewall cannot prevent attacks that do not pass through the firewall or bypass the firewall. For example, some users may form a direct connection to the Internet if they are allowed to dial out from inside the protected network. Firewalls are based on packet header information detection and blocking methods, mainly access control of services provided or requested by hosts, and cannot block harmful traffic flowing through open ports, and are not a solution to worms or hacking attacks. In addition, it is difficult for firewalls to prevent attacks or abuses from within the network.
Table of Contents
ToggleRelated Products:
-
 Palo Alto Networks PAN-SFP-PLUS-SR Compatible 10G SFP+ SR 850nm 300m LC MMF DDM Transceiver Module
$12.00
Palo Alto Networks PAN-SFP-PLUS-SR Compatible 10G SFP+ SR 850nm 300m LC MMF DDM Transceiver Module
$12.00
-
 Palo Alto Networks PAN-SFP-PLUS-LR Compatible 10G SFP+ LR 1310nm 10km LC SMF DDM Transceiver Module
$18.00
Palo Alto Networks PAN-SFP-PLUS-LR Compatible 10G SFP+ LR 1310nm 10km LC SMF DDM Transceiver Module
$18.00
-
 Palo Alto Networks PAN-SFP-PLUS-T Compatible 10G Copper SFP+ 30m RJ45 without DDM Transceiver Module
$45.00
Palo Alto Networks PAN-SFP-PLUS-T Compatible 10G Copper SFP+ 30m RJ45 without DDM Transceiver Module
$45.00
-
 Fortinet FG-TRAN-QSFP+SR Compatible 40G QSFP+ SR4 850nm 150m MTP/MPO MMF DDM Transceiver Module
$25.00
Fortinet FG-TRAN-QSFP+SR Compatible 40G QSFP+ SR4 850nm 150m MTP/MPO MMF DDM Transceiver Module
$25.00
-
 Fortinet FG-TRAN-QSFP+LR Compatible 40G QSFP+ LR 1310nm (CWDM4) 10km LC SMF DDM Transceiver Module
$149.00
Fortinet FG-TRAN-QSFP+LR Compatible 40G QSFP+ LR 1310nm (CWDM4) 10km LC SMF DDM Transceiver Module
$149.00
-
 Fortinet FG-TRAN-QSFP-4XSFP-5 Compatible 5m (16ft) 40G QSFP+ to Four 10G SFP+ Active Optical Breakout Cable
$89.00
Fortinet FG-TRAN-QSFP-4XSFP-5 Compatible 5m (16ft) 40G QSFP+ to Four 10G SFP+ Active Optical Breakout Cable
$89.00
-
 Palo Alto Networks PAN-QSFP-AOC-5M Compatible 5m (16ft) 40G QSFP+ to QSFP+ Active Optical Cable
$75.00
Palo Alto Networks PAN-QSFP-AOC-5M Compatible 5m (16ft) 40G QSFP+ to QSFP+ Active Optical Cable
$75.00







